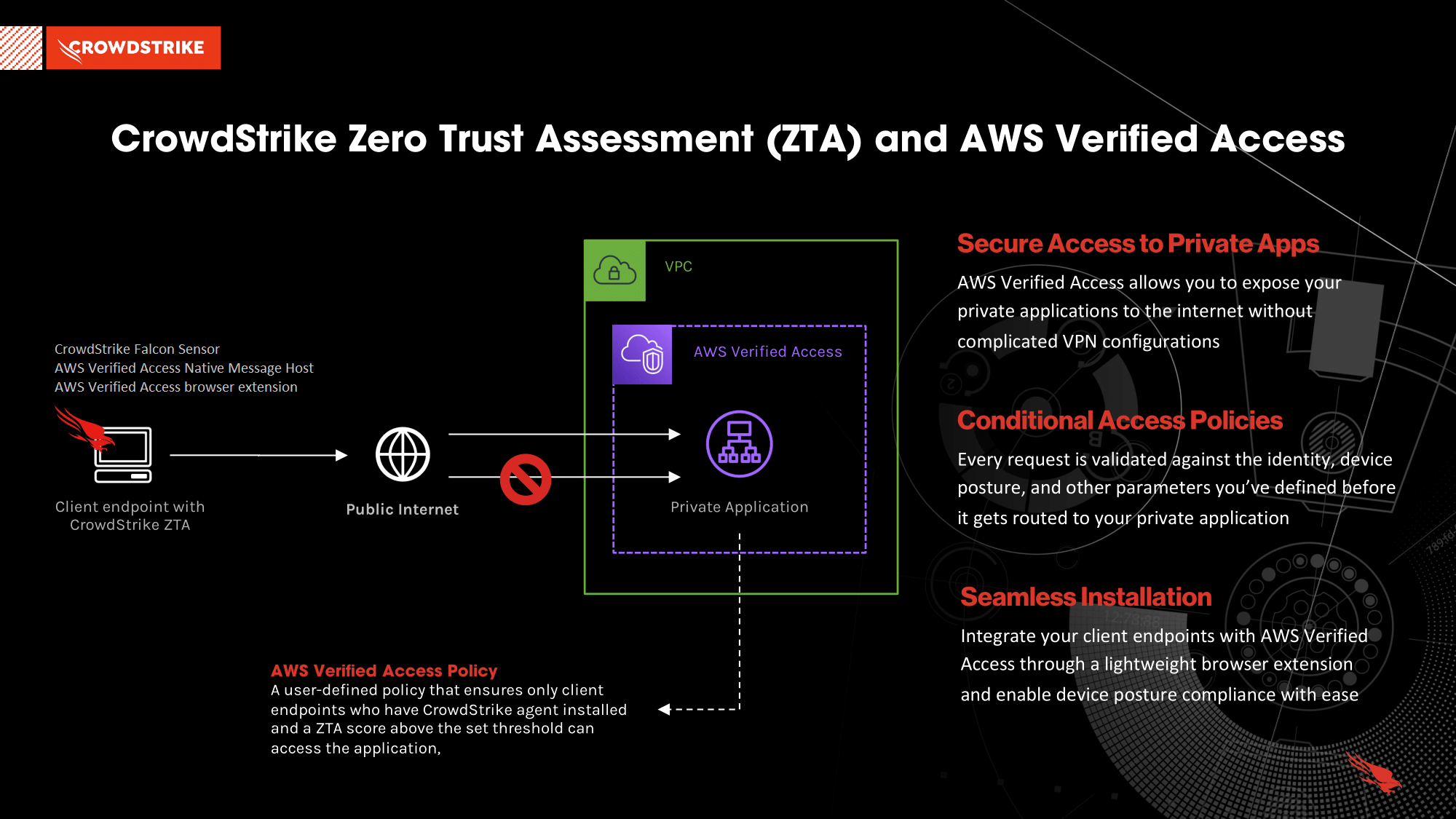
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access - crowdstrike.com

IAM makes it easier for you to manage permissions for AWS services accessing your resources | AWS Security Blog

IAM makes it easier for you to manage permissions for AWS services accessing your resources | AWS Security Blog
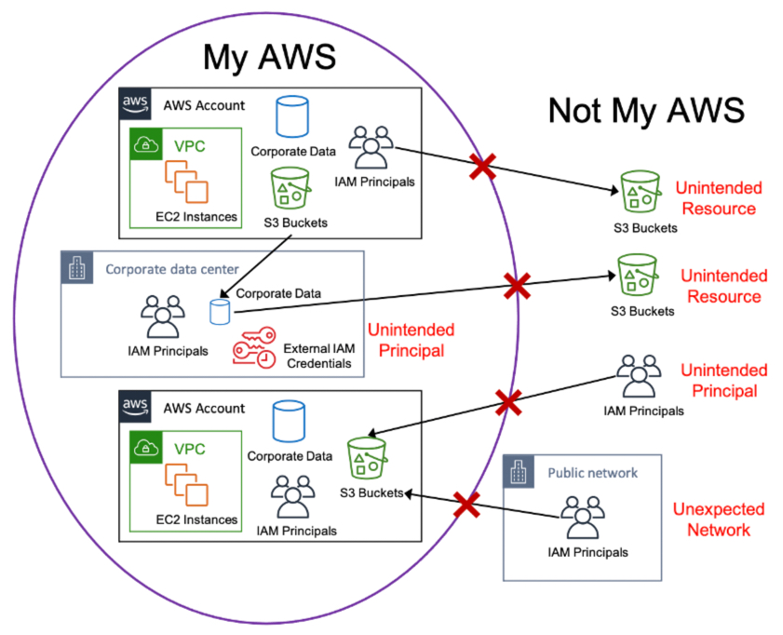
Jeff Barr ☁️ (@ 🏠 ) 💉 on Twitter: "#AWS for Industries: Using AWS Services to Protect Against, Detect, and Respond to Unauthorized Data Access - https://t.co/gWdsSdIgM8 The intent is to design

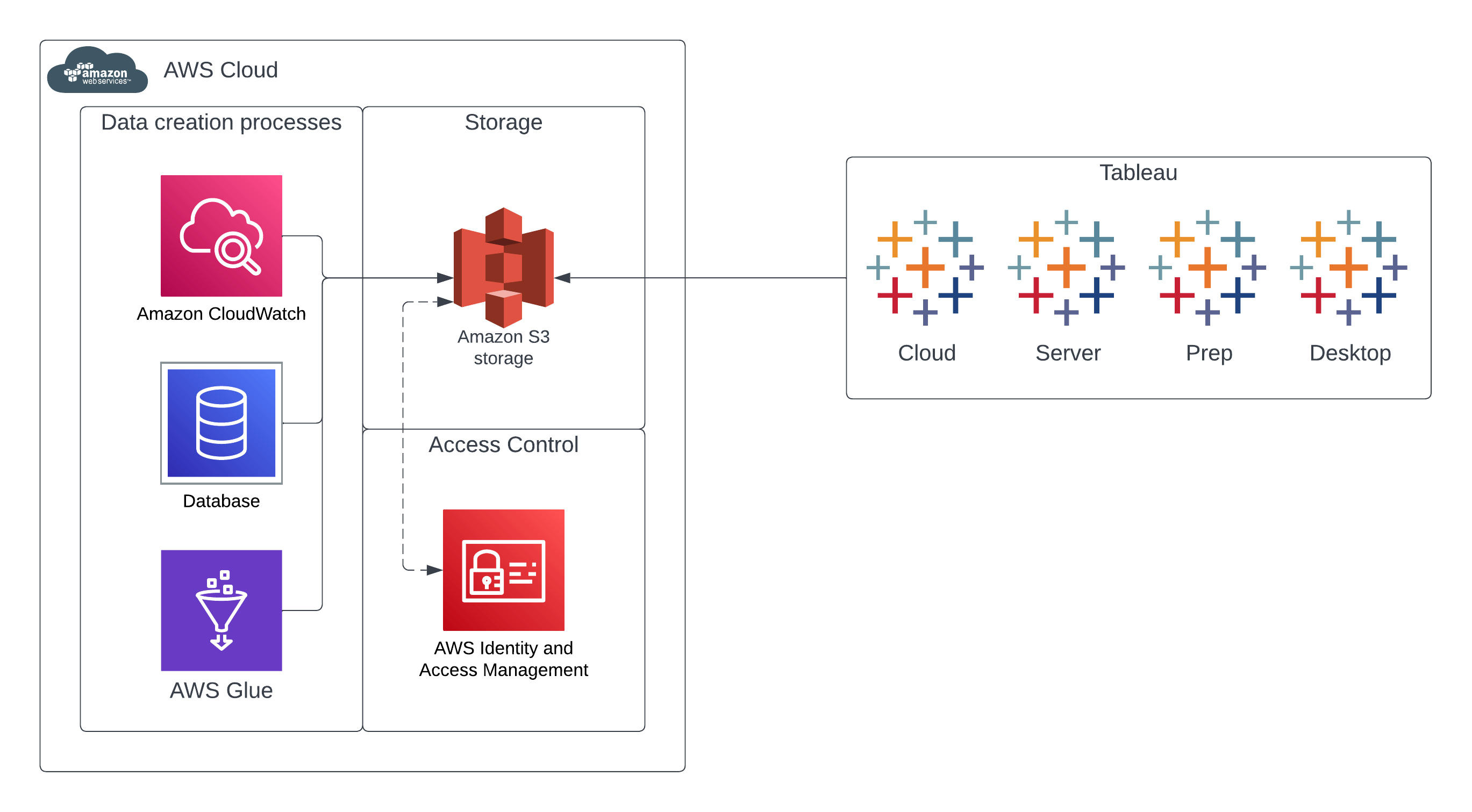
Enable cross-account access for Amazon SageMaker Data Wrangler using AWS Lake Formation | AWS Machine Learning Blog