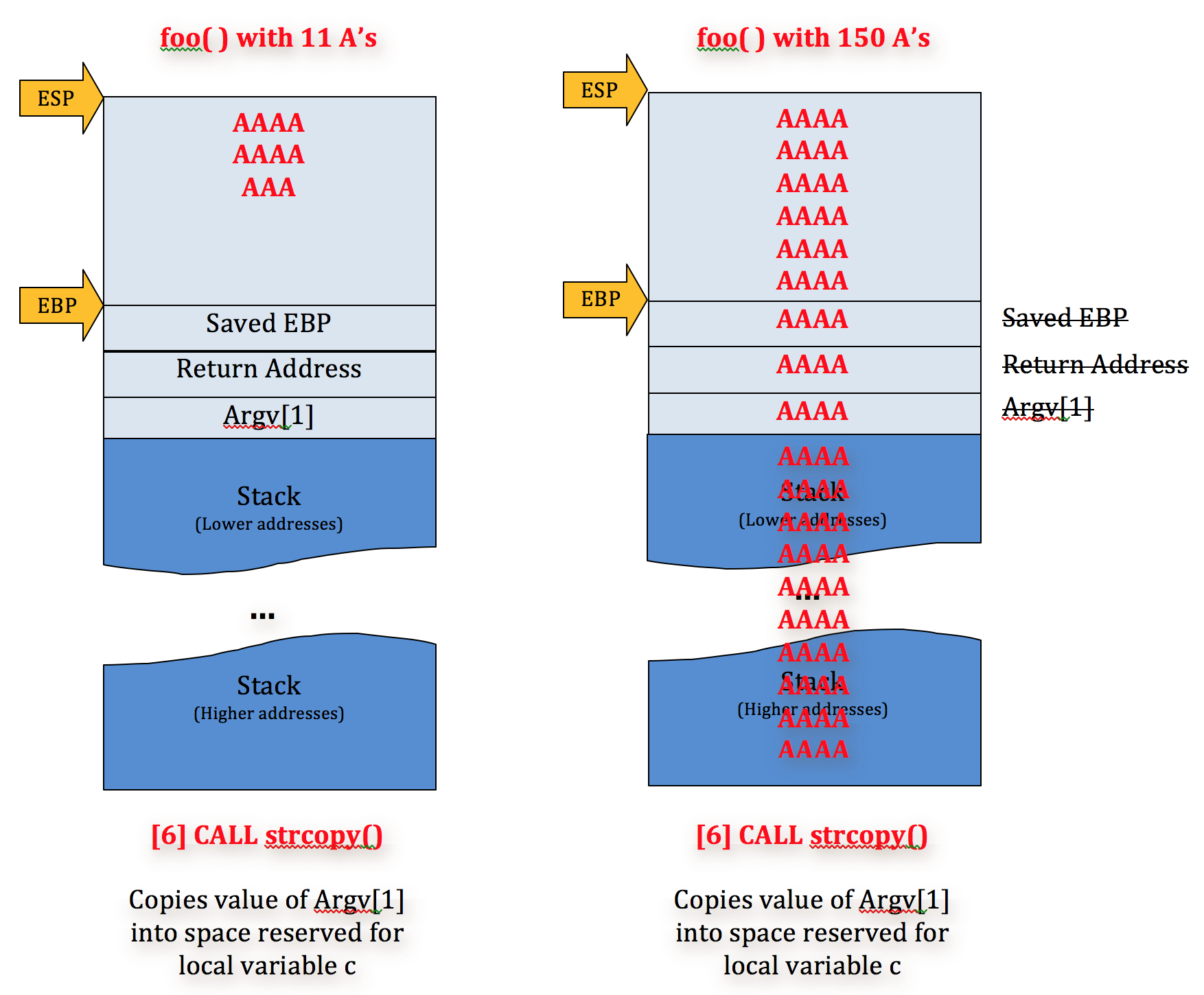
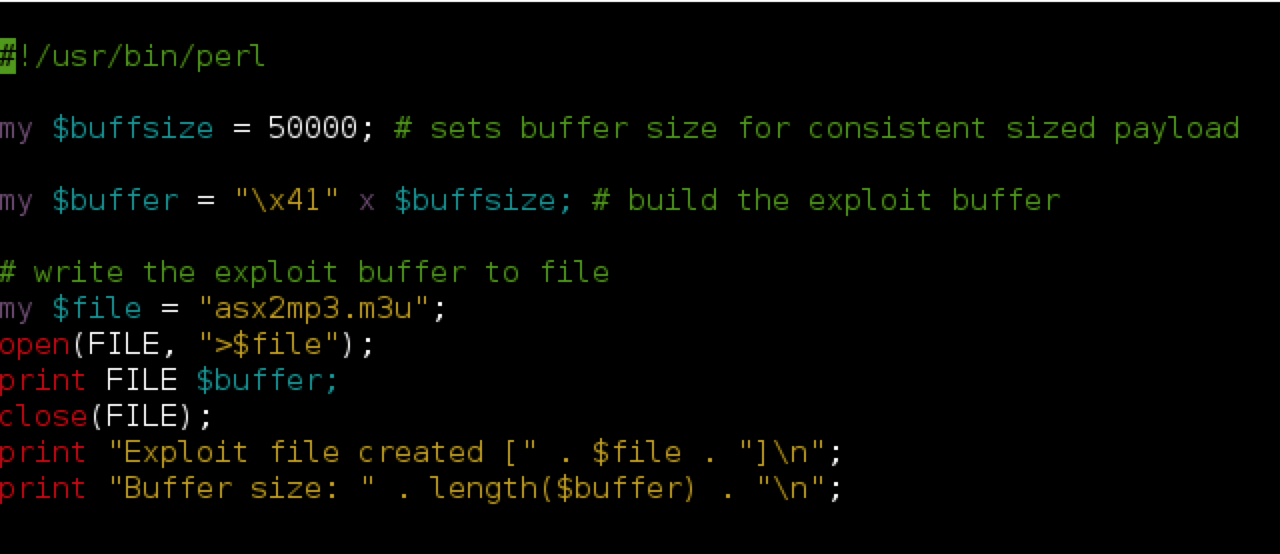
Multiple Vulnerabilities in Perl https://www.cert-in.org.in/ Severity Rating: Medium Software Affected · Perl versions pri

Stack Based Buffer Overflow Practical For Windows (Vulnserver) | by Shamsher khan | InfoSec Write-ups

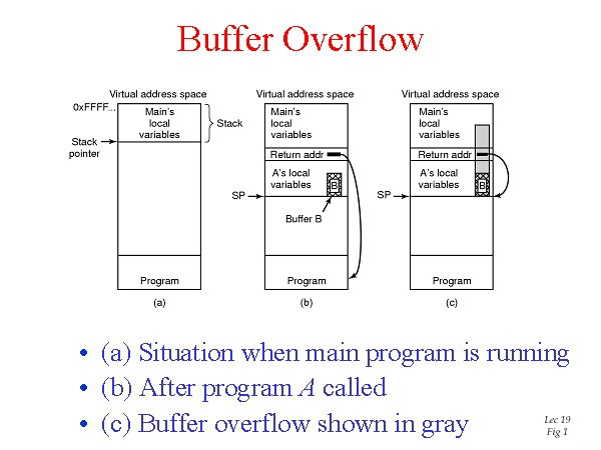
Buffer Overflow. Introduction On many C implementations, it is possible to corrupt the execution stack by writing past the end of an array. Known as smash. - ppt download