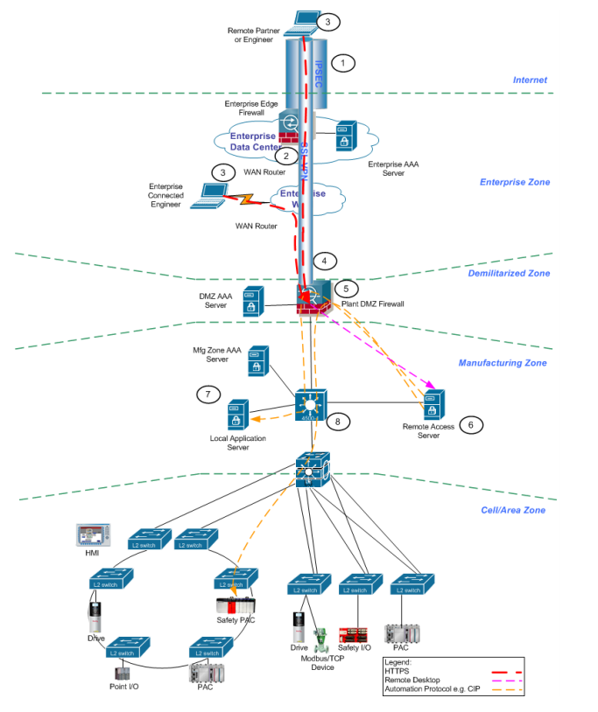
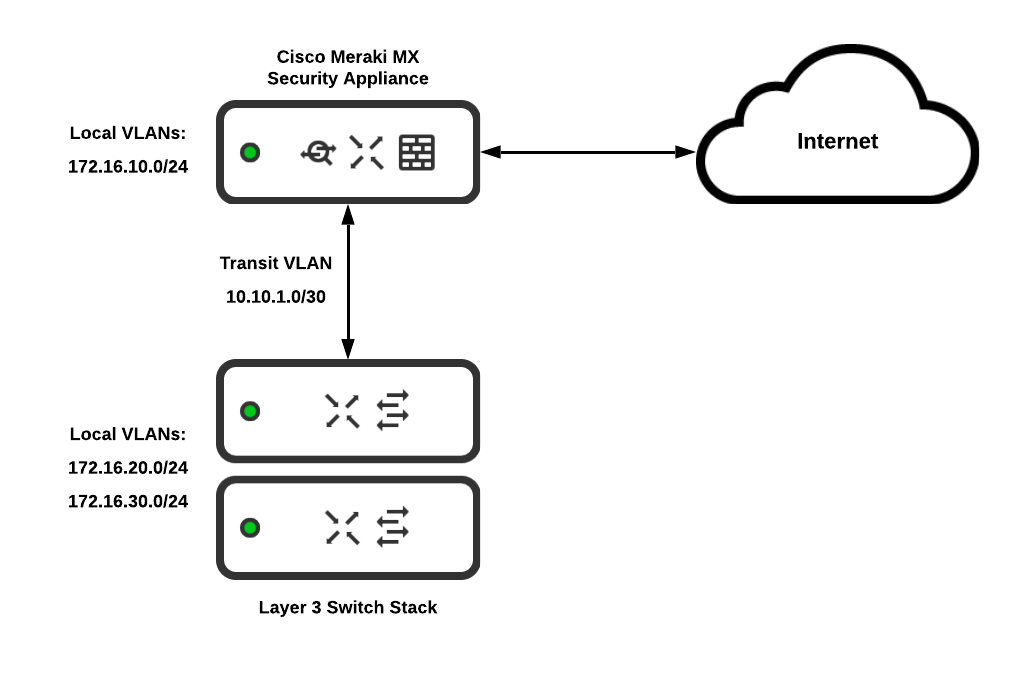
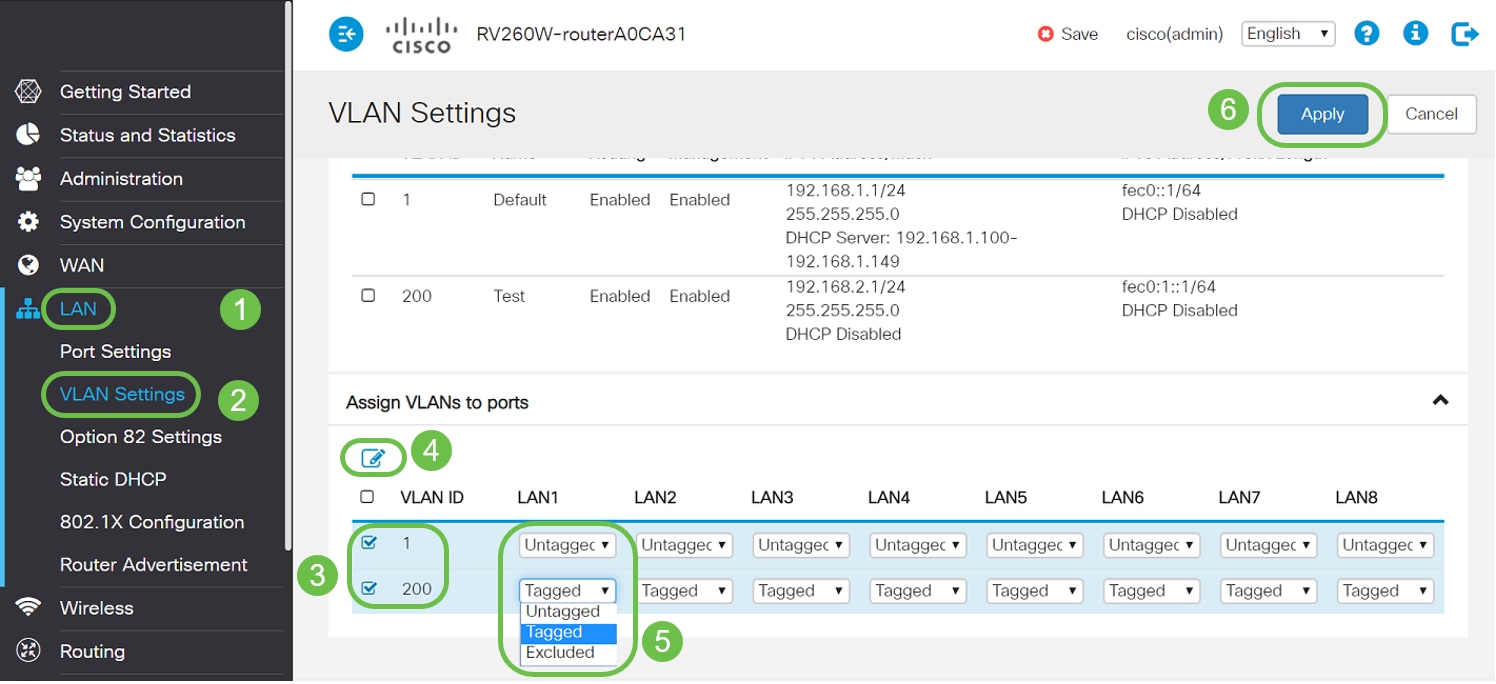
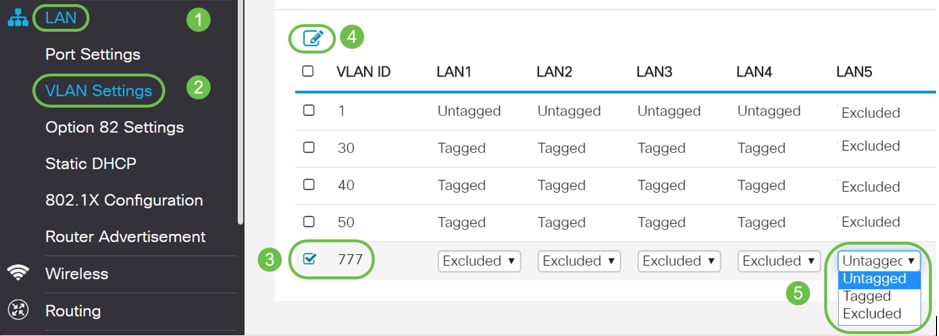
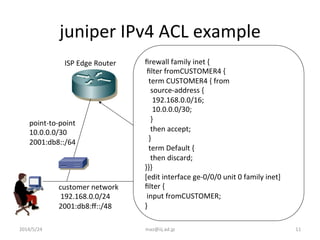
Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press
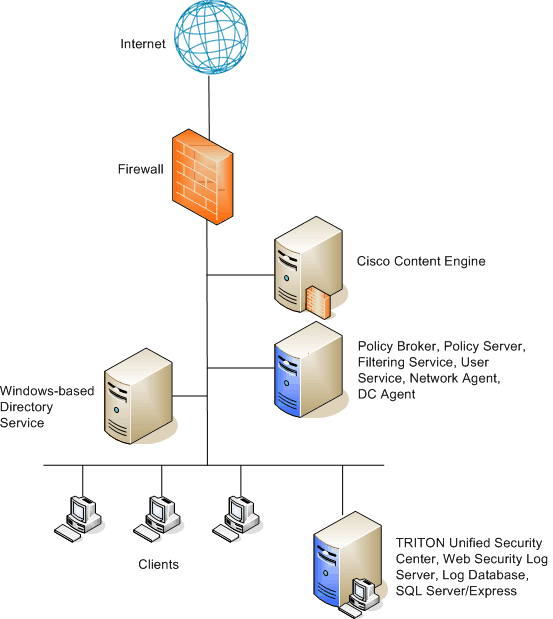
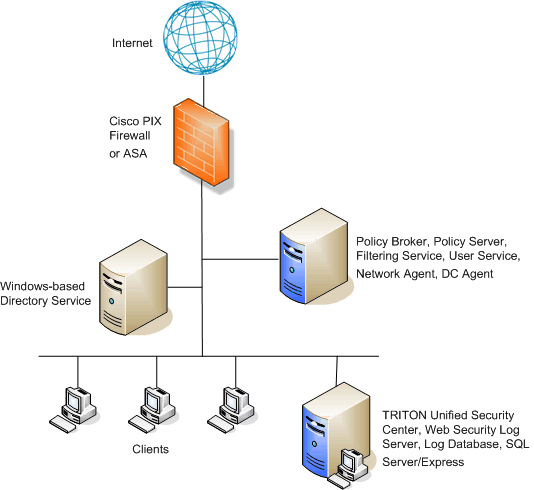
PDF) Hardening CISCO Devices based on Cryptography and Security Protocols - Part II: Implementation and Evaluation