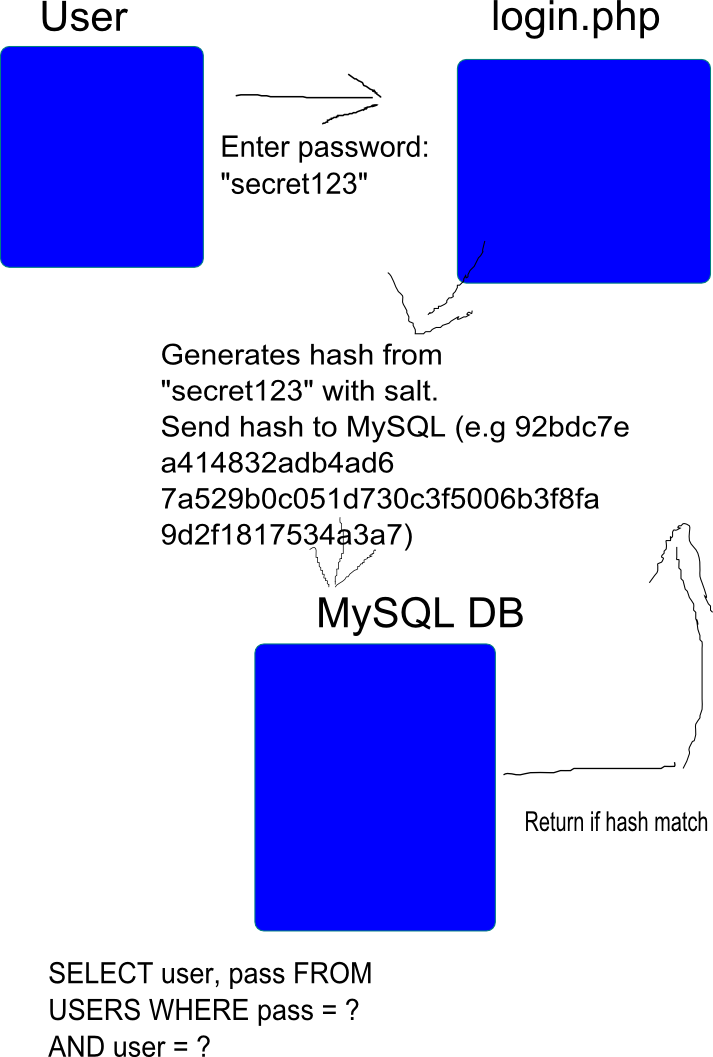
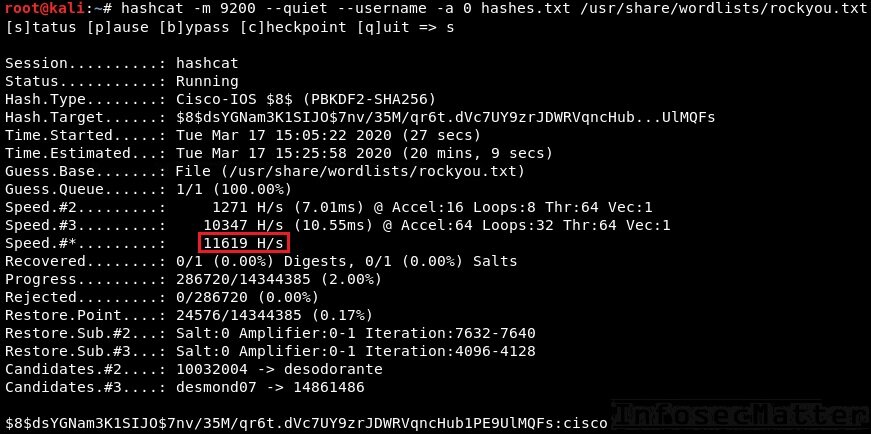
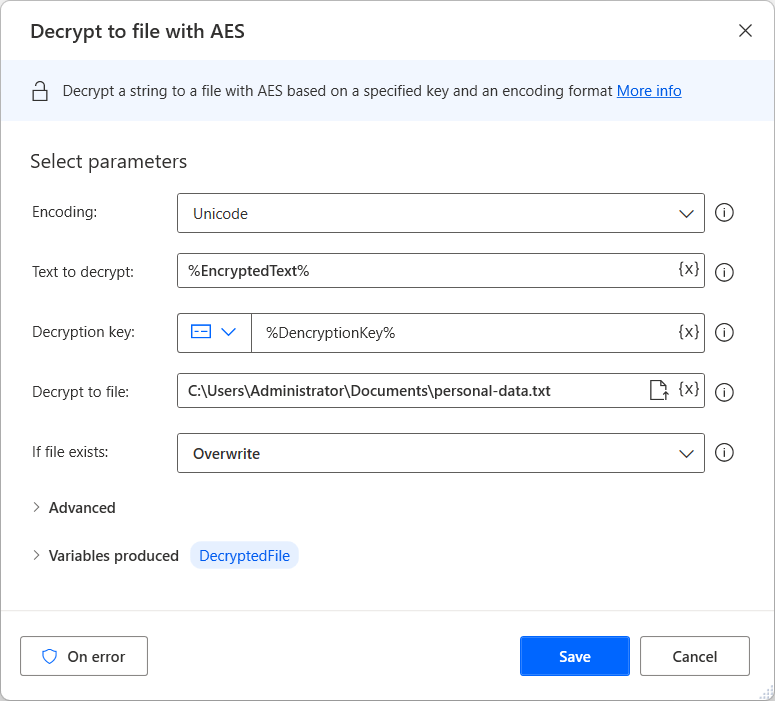
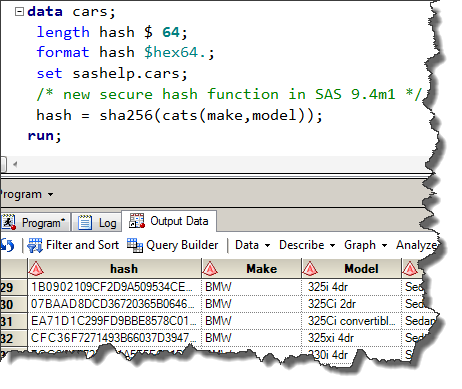
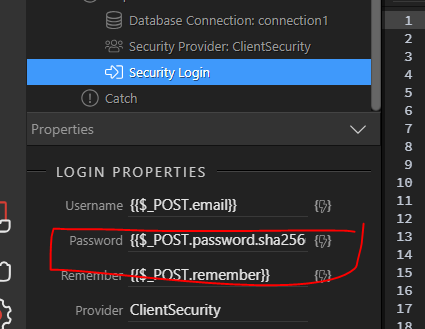
SHA 256: Compute a SHA 256 hash using C# for effective security - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds
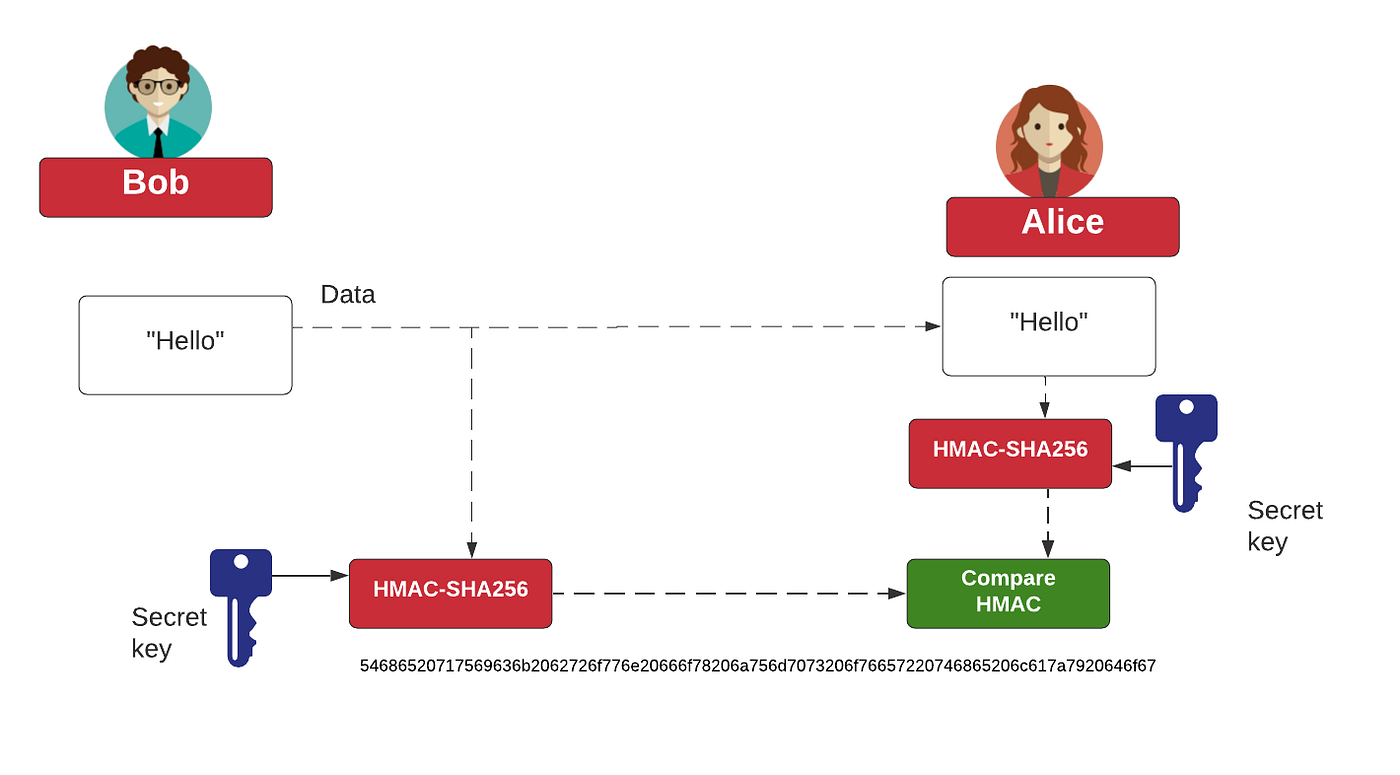
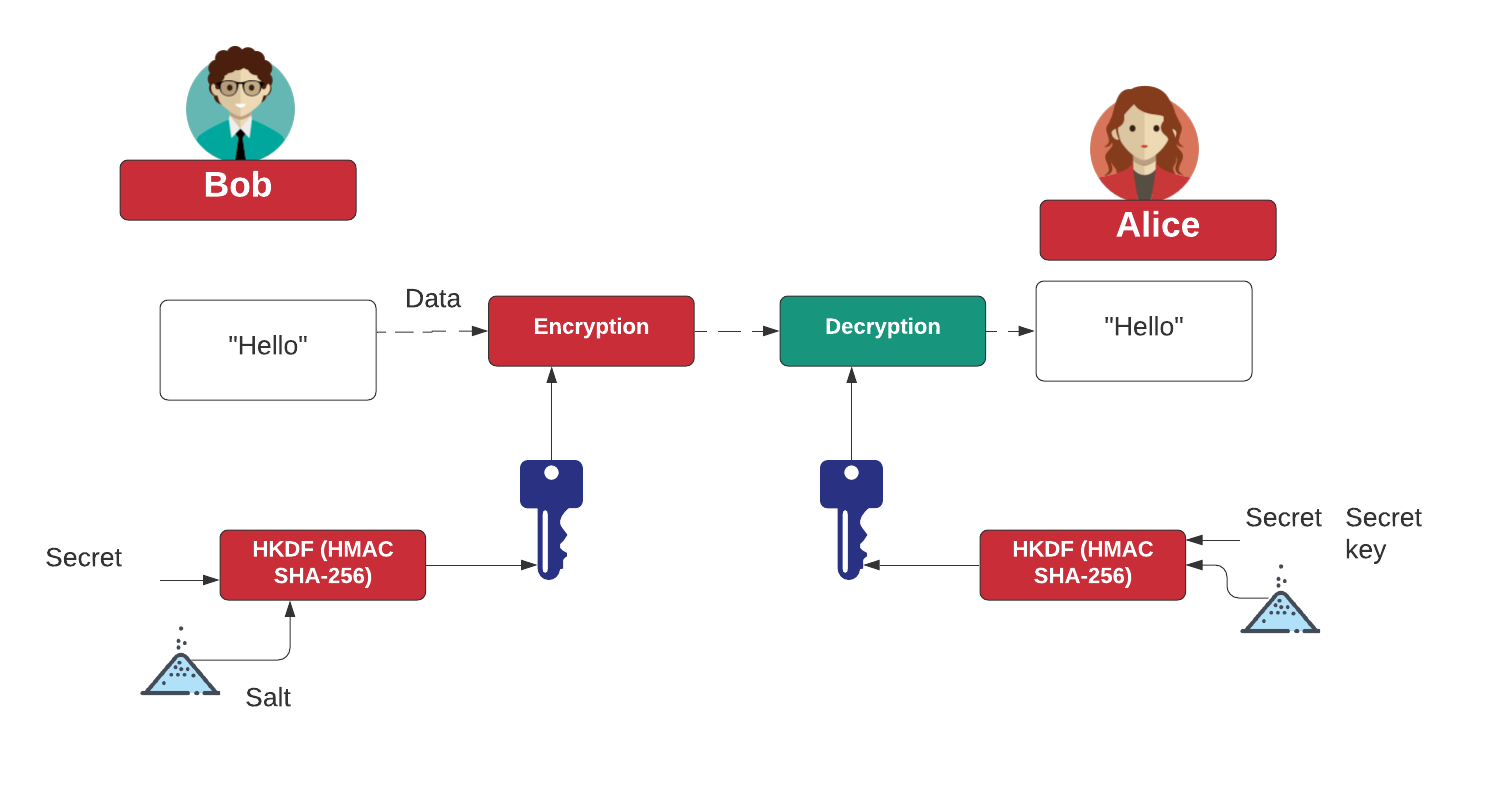
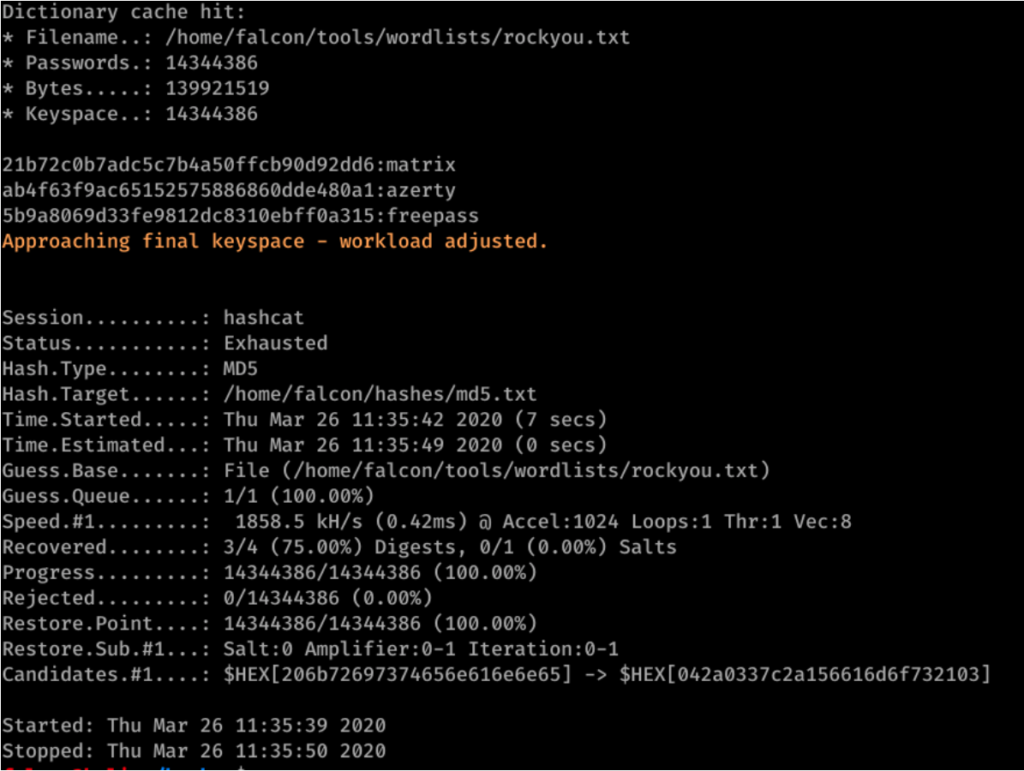
HMAC and HKDF. What's the right way to correct an… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

java - Encryption and Decryption with PBKDF2 and AES256 - practical example needed - how do I get the Derived key - Stack Overflow
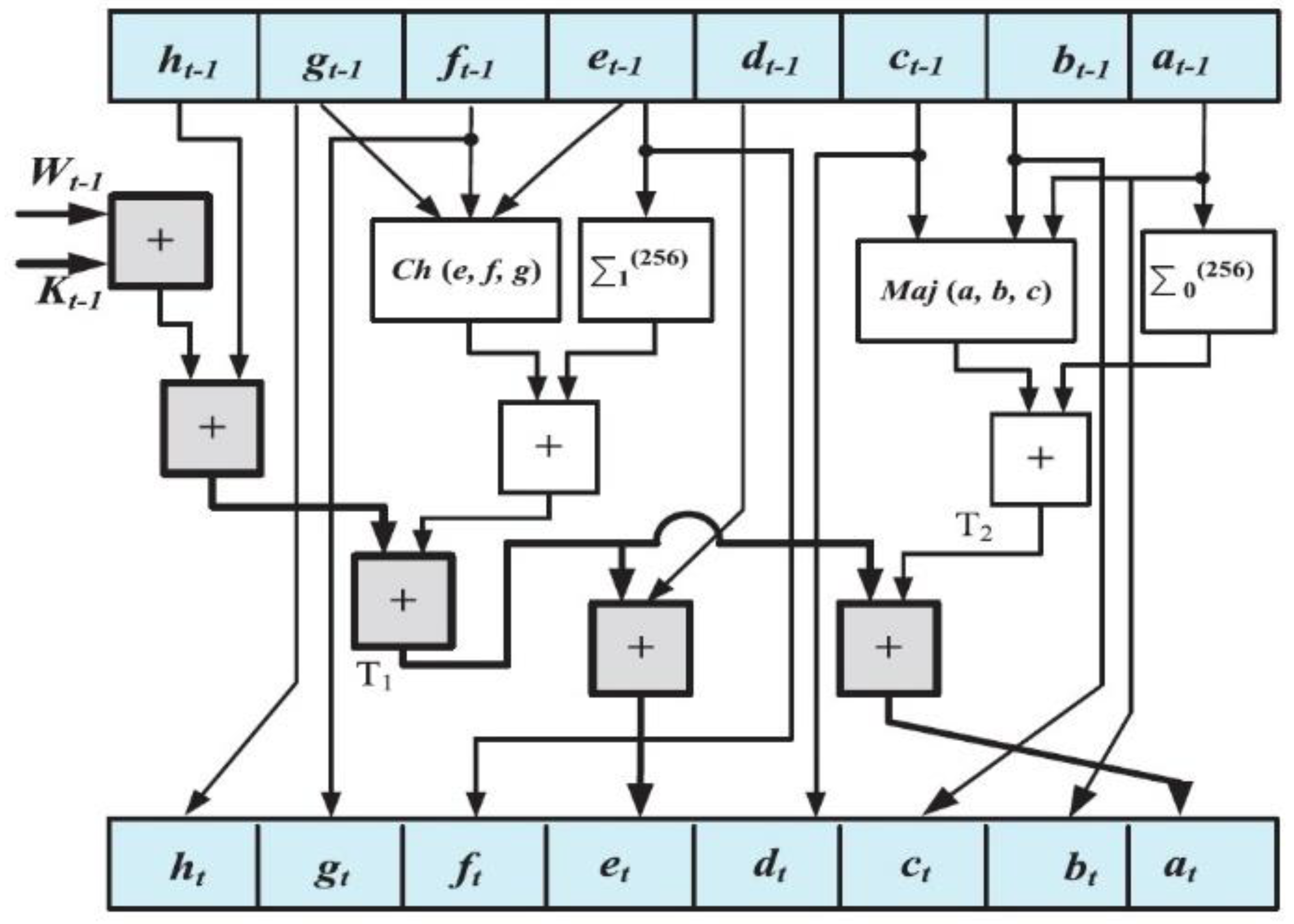
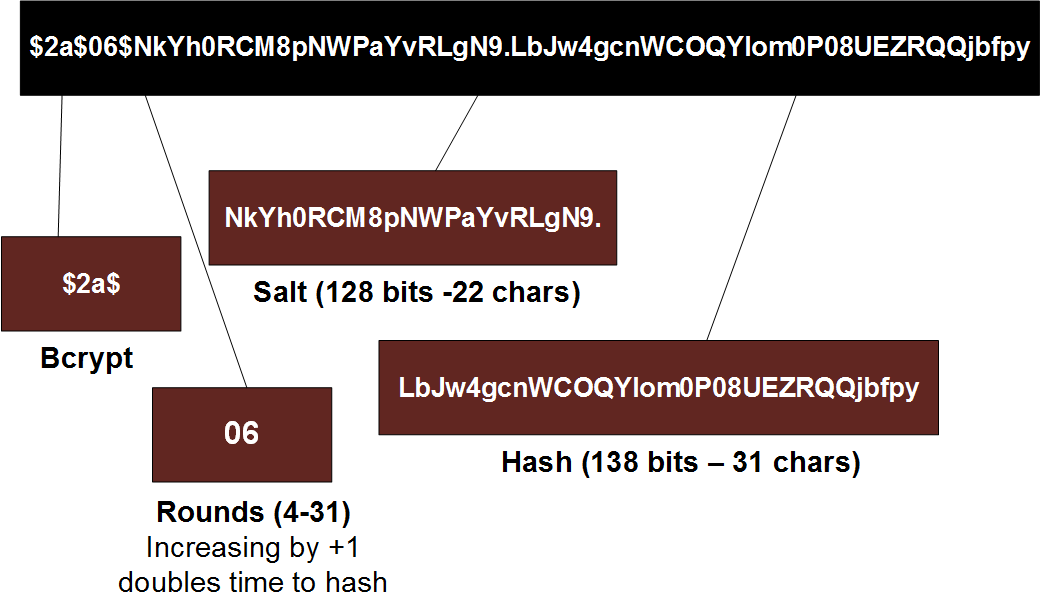
Entropy | Free Full-Text | A New Algorithm for Medical Color Images Encryption Using Chaotic Systems